Governance, risk, and compliance (GRC) data has always been a challenge for financial entities, critical infrastructure providers, and organizations in highly regulated industries. But the compliance environment in 2025 is fundamentally different.
- The EU’s Digital Operational Resilience Act (DORA), which took effect on 17 January 2025, obliges financial institutions to prove digital resilience across their technology stack. It is no longer enough to simply document risk processes—firms must evidence operational resilience in near real-time.
- The EU Network and Information Security Directive (NIS2), which required Member States to transpose requirements by 17 October 2024, significantly broadened the scope of incident reporting and risk management across energy, transport, healthcare, cloud, public administration, and other critical sectors.
Together, these two frameworks are pushing organizations toward a new standard of GRC data portability, interoperability, and auditability. No more brittle spreadsheets, siloed data exports, or last-minute evidence scrambles. Regulators expect lineage, timeliness, and trustworthiness in every data point.
The solution? A resilient GRC data pipeline designed with standardization (OSCAL), streaming ingestion, governed warehousing, and automated lineage.
Why Standardization Matters: OSCAL as the Canonical Language
The first step to resilience is removing translation friction. Every GRC program involves multiple data sources:
- ITSM platforms (e.g., ServiceNow, Jira Service Management) capturing incidents, changes, and assets.
- IRM/GRC suites (e.g., Archer, OneTrust, ServiceNow GRC) tracking policies, risks, controls, and attestations.
- Cloud providers exposing security posture via APIs.
- Scanners & monitoring tools (vulnerability management, SIEM, CSPM) generating findings and alerts.
Without a shared schema, every integration requires brittle one-off mappings. That’s where NIST OSCAL (Open Security Controls Assessment Language) comes in.
- Machine-readable formats: XML, JSON, YAML.
- Predefined schemas for control catalogs, system security plans (SSPs), assessment plans, and results.
- Recent innovations include control mapping models with confidence scores, allowing frameworks (e.g., ISO 27001 ↔ SOC 2 ↔ PCI DSS) to be translated at scale.
By making OSCAL the canonical exchange format, organizations can:
- Avoid re-mapping risks, controls, and test procedures every audit cycle.
- Ensure semantic consistency (a “control” means the same thing across ServiceNow, Archer, and Snowflake).
- Generate auditor-ready subsets (CSV/JSON) without losing lineage.
Real-Time Ingestion vs. Quarterly Crunch
Historically, compliance evidence has been collected quarterly or annually, just before audits. But under DORA and NIS2, that model fails:
- DORA requires firms to demonstrate continuous resilience—not a once-a-year snapshot.
- NIS2 sets strict incident-reporting deadlines (as little as 24 hours for initial notifications).
That means GRC pipelines must stream, not batch.
Example: Snowflake’s Streaming Ingest
- Snowpipe: loads staged files within minutes.
- Snowpipe Streaming: row-level, low-latency ingestion directly into warehouse tables.
With this approach:
- KRIs/KPIs update in real-time (e.g., number of open critical vulnerabilities, failed backups, overdue risk exceptions).
- Dashboards for executives and auditors reflect the current state of resilience.
- Organizations can meet tight reporting windows without manual crunches.
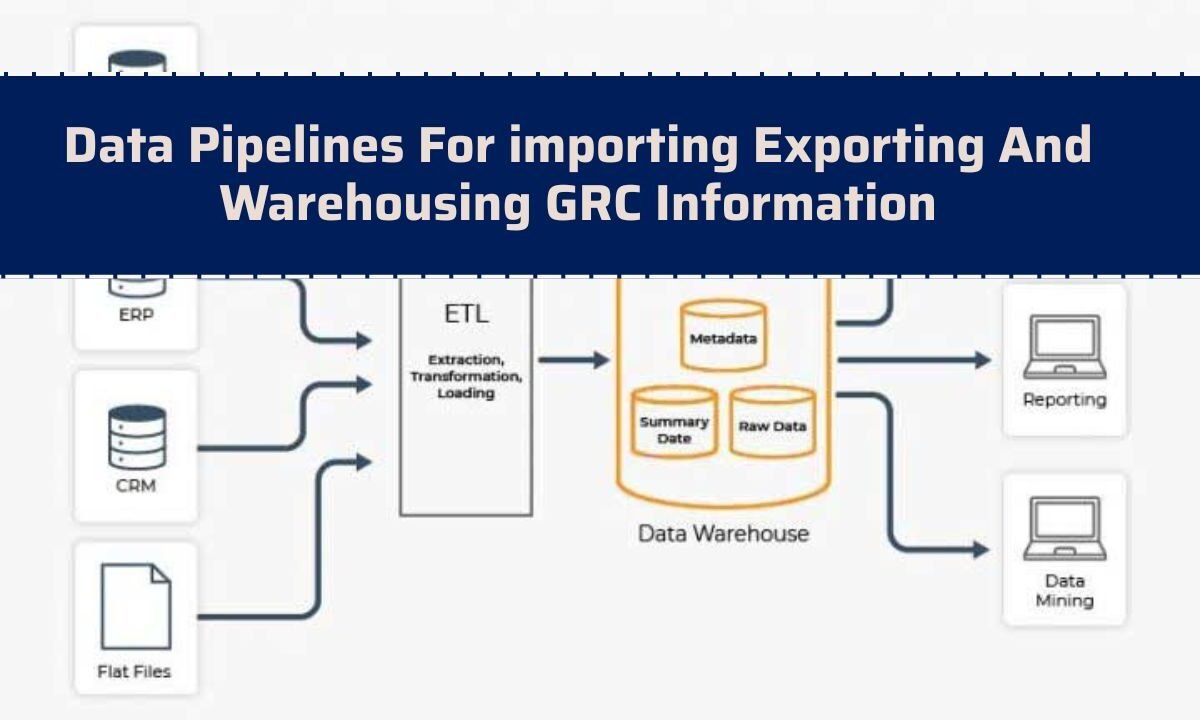
Reference GRC Pipeline: From Source to Auditor
| Stage | Purpose | Tech Examples | Artifacts & Formats |
|---|---|---|---|
| Ingest (Import) | Land raw events, assets, assessments | Cloud storage, APIs, queues, Snowpipe/Streaming | Logs, findings, attestations, CSV/JSON, OSCAL packages |
| Staging | Validate, deduplicate, PII tagging | Object storage + staging schemas | Hashes, checksums, PII flags, source IDs |
| Transform (ELT) | Normalize, map frameworks | SQL/DBT, notebooks, UDFs | Control mappings, risk registers, test procedures |
| Warehouse | Analytics & evidence marts | Snowflake, BigQuery, Redshift | “Single source of truth” marts with lineage |
| Export (Out) | Share with auditors & tools | API push, secure shares, files | OSCAL assessments, scoped CSVs, reports |
| Govern | Secure & track | IAM/RBAC, masking, policy engines | Retention SLAs, access logs, approvals |
This reference model ensures every control test, risk entry, and evidence file is traceable, versioned, and secured.
Design Principles That Pass Audits
- Canonical Model (OSCAL)
Reduces one-off mappings and ensures semantic consistency. - ELT > ETL
Keep raw evidence in your warehouse for reproducibility; transform with DBT/SQL/UDFs for audit trails. - Automated Lineage
Every artifact should be traceable to:- Source system (e.g., ServiceNow table).
- User or API account.
- Timestamp of extraction.
- Streaming Where it Matters
Use low-latency pipelines for high-value KRIs like failed backups or open critical vulnerabilities. - Hardened Exports
Version every OSCAL/CSV package. Digitally sign artifacts. Log who exported what and when. - Secure by Design
- RBAC enforcement.
- Column-level masking for PII.
- Retention policies aligned with DORA/NIS2 regulatory clocks.
Example Implementation Checklist
- Framework Mapping: Align ISO 27001, SOC 2, PCI DSS, and NIST CSF to OSCAL.
- Source Inventory: Catalog ServiceNow GRC, vulnerability scanners, CSPM APIs.
- Streaming Ingest: Deploy Snowpipe Streaming for critical evidence.
- Staging Validation: Deduplicate, tag PII, enforce schema consistency.
- Evidence Marts: Build semantic models for risks, controls, and issues.
- Automated Exports: Push OSCAL/CSV packages to auditors and upstream tools.
- Monitoring & Alerts: Track data freshness, completeness, and access anomalies.
Risks of Non-Compliance
Organizations that fail to modernize their pipelines face multiple risks:
- Regulatory fines under DORA/NIS2 for delayed or inaccurate reporting.
- Operational risk if resilience gaps go undetected due to stale data.
- Audit fatigue from repeated manual evidence collection.
- Reputational damage if incident disclosures reveal lack of data governance.
Future-Proofing Your GRC Pipeline
As regulatory expectations continue to evolve, resilient pipelines should be designed for:
- Multi-framework mapping: Align DORA, NIS2, ISO 27001, PCI DSS, and emerging ESG standards.
- AI-driven anomaly detection: Spot gaps in control testing or unusual incident patterns.
- Interoperability with AI auditors: Regulators may begin consuming OSCAL directly for automated review.
- Privacy-first designs: As GDPR and similar laws tighten retention rules, policy-driven masking and deletion will become critical.
With OSCAL-based standardization, streaming ingestion, and a governed data warehouse, organizations can finally meet the heightened expectations of DORA and NIS2. The result isn’t just compliance—it’s a real-time, audit-ready view of resilience.
Instead of brittle spreadsheets and last-minute scrambles, your team operates from a single source of truth, where risks, controls, and evidence are always current. Regulators get what they want: lineage, trust, and timeliness. And your organization gets what it needs: resilience, visibility, and peace of mind.
FAQs
Use OSCAL as the canonical model, then generate CSV/JSON for specific auditors or tools.
For critical KRIs (like failed backups), aim for minutes. For policy reviews, nightly batches may suffice.
Yes. Structured data, automated lineage, and timely reporting directly satisfy digital resilience and incident-reporting requirements.