Trusted Integration, Inc.
107 S. West Street, Ste. 146, Alexandria, Virginia 22314
Phone: 703-299-9171 | Fax: 703-299-9172
107 S. West Street, Ste. 146, Alexandria, Virginia 22314
Phone: 703-299-9171 | Fax: 703-299-9172
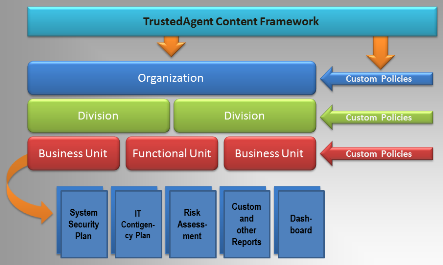
TrustedAgent content framework offers organizations with the maximum possibilities to support regulations, policies, standards, or controls in one central location, to communicate, and ensure implementation of the controls to lower units including divisions, business or functional units, subsidiaries, or vendors within and external to the organizations.
TrustedAgent content framework, pictured below, contains information supporting a full lifecycle of any risk and compliance management process. TrustedAgent content framework comprises of two major components: TrustedAgent Control Content and TrustedAgent Authorization Content.
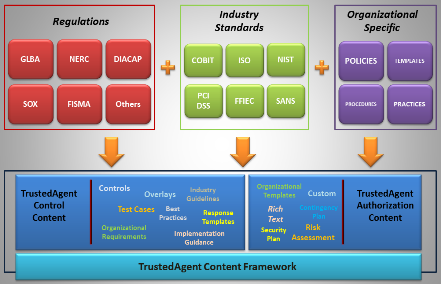
The control content, shown above, manages data associated with the controls to the TrustedAgent Platform, and delivers these content along with user information and the authorization content, as shown below, as templates for reporting.